
To stop ransomware and other malicious behaviors, you need to do more than look for threats. Reduce your surface areas of attack with policy-driven endpoint security and change the paradigm from only blocking threats, to blocking everything that is not trusted. Combined with Ringfencing and storage policies, you enhance your zero-trust protection and block attacks that live off the land.
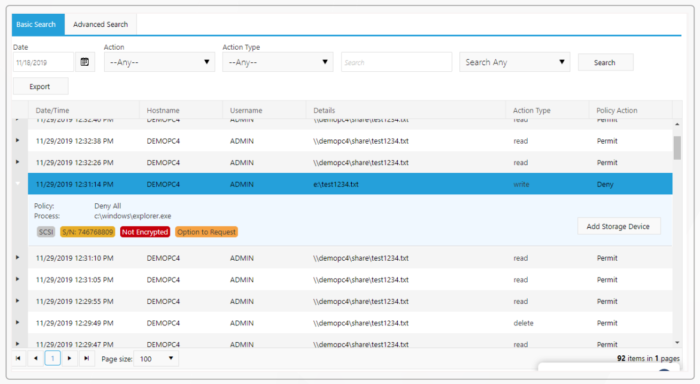
Full Detailed Audit
Full granular audit of every application, library, and script opened in realtime, including the computer, hash, certificate, process, and user that opened it. When combined with storage policies, full details of all files and documents accessed, changed, deleted, or moved are recorded in the audit in realtime.
Block by Default
Application Whitelisting is the gold standard in protecting against ransomware, viruses, and other malicious software. The ThreatLocker solution combines advanced software and service, allowing you to deploy application whitelisting in a few hours, without the management overhead.
Our 24-hour operations center continuously monitors for application and operating system updates, so you do not have to worry about adding every new file to the Application Whitelist every time that Microsoft, Google, or another Vendor releases an update.